Google Rapid Response (GRR)
Created By: Farr, Collin
93 Cyber Protection Team
collinfarr2@gmail.com
GRR Rapid Response is an incident response framework focused on remote live forensics. It consists of a python client (agent) that is installed on target systems, and python server infrastructure that can manage and talk to clients. The goal of GRR is to support forensics and investigations in a fast, scalable manner to allow analysts to quickly triage attacks and perform analysis remotely.
Creating GRR From Install:
Installing OS (Red Hat Enterprise Linux Version - 6.9 & <)
-
Download the RHEL v.X.x Binary DVD From:
https://access.redhat.com/downloads/content/69/ver=/rhel---7/7.5/x86_64/product-software - Create a new virtual machine (VM) template with desired virtualization software using Binary DVD.iso
- Be sure to allocate enough resources for GRR depending on size of desired deployment (i.e. if deploying to 20+ endpoint hosts be sure to make the hard drive space large enough to be able to store all hunts).
-
Once the VM is booted a few configuration changes need to be made:
-
Date/Timeshould be set to Coordinated Universal Time (UTC). -
Under the
Installation Sourcesection: Verify the media the install is coming from. * Be sure the media is selected before continuing. -
Under “Software Selection”: * “Minimal Install” should be selected along with the add-ons “Development Tools” and “Compatible Libraries”.
-
Verify “Installation Location” is correct. (It should be the virtual disk from the creation of the VM.
-
Under “Network & Hostname” check to be sure the ethernet interface is present. These settings will be configured later.
- Hit Next to start the install of the operating system. * Be sure to verify that the root account password is set.
Configuring Red Hat For GRR
-
Determine the name of the network interface for the VM (usually along the lines of eth0 or ens33) #ip addr
-
Configure the configuration file for that interface. #vi /etc/sysconfig/network-scripts/ifcfg-
- The following configurations should replace what is already in the config file.
DEVICE=
BOOTPROTO= |none , static| ONBOOT=yes PREFIX=24 IPADDR= NETWORK= NETMASK=<255.255.255.0> GATEWAY= - Save this file and exit vi :wq!
- Using ifdown and ifup restart the interface.
#ifdown
#ifup - Edit Resolv.conf file to add nameservers. #vi /etc/resolv.conf
- Add the following to the configuration file nameserver 8.8.8.8 nameserver 8.8.4.4
- Check for network connectivity by pinging the default gateway and then external network
- NOTE To check for external network connectivity pinging Google’s DNS is always a safe option. (8.8.8.8)
- Configure RHEL to utilize repositories.
- Register The RHEL Instance. #subscription-manager register User: Password:
- Download and configure the Epel-repo. #rpm -ivh https://dl.fedoraproject.org/pub/epel/epel-release-latest-7.noarch.rpm # yum update
- Configure the firewall to allow HTTP connections to the VM.
- Check to see if firewalld is running using #firewall-cmd –state
- Once verified the firewall is running check the allowed services for “HTTP” #firewall-cmd –get-services | grep http
- If http is not allowed add to list of services and make persistent using using: #firewall-cmd –add-service=http #firewall-cmd –runtime-to-permanent
- If http is allowed continue.
- Add the GRR web interface ports to allowed ports list. # firewall-cmd –add-port=8000/tcp # firewall-cmd –add-port=8080/tcp # firewall-cmd –runtime-to-permanent
Installing GRR (using pip).
-
Using Yum install the needed dependencies: # yum install -y epel-release python-devel wget which libffi-devel openssl-devel zip git gcc gcc-c++ redhat-rpm-config
# yum install -y python-pip -
Using pip install grr-response-server: # pip install grr-response-server
Configuring GRR.
- Create the initial GRR configuration file
# grr_config_updater initialize
- The RSA Keys will automatically generate for GRRs configurations.
- Choosing a(n) SQL version.
#1
- Configure the Datastore Location. (The default is fine but is able to be changed)
- If using a unique hostname, enter that next.
- Frontend and Admin UI server URL. If using DNS to reach back to the GRR Server, add that domain here otherwise use the static ip that is set:
http://x.x.x.x:8080/ (Front End)
http://x.x.x.x:8000/ (Admin UI)
- If using a mail server to receive GRR alerts correctly input that information here
- Rekall is no longer supported, do not enable it.
#n
- Adding The Admin user. (Set the admin users password)
- Download Client Templates.
#Y
- Repack the Client Templates.
#Y
Starting GRR to a Running State.
- Using the commands added by GRR deploy the individual services.
- Using the ‘&’ will run the command in the background #grr_admin_ui & #grr_worker & #grr_frontend &
- Attempt to connect to the UI from a host within the network using the set addresses in the configuration file.
If Attempted connection fails:
- Attempt to Ping the GRR server to verify traffic gets to the destination.
- Double check the IP address of the Server against what is in the configuration.
- Attempt to Ping from the GRR Server out into the host team internal network.
- Double check that all firewalld rules and implementations have been set correctly.
Deploying GRR Agents.
For Windows Operating systems (Psexec):
- Determine whether the hosts are 32 or 64 bit operating systems
- Download the respective agent from the web ui.
- Under the configuration section select ‘Manage Binaries’
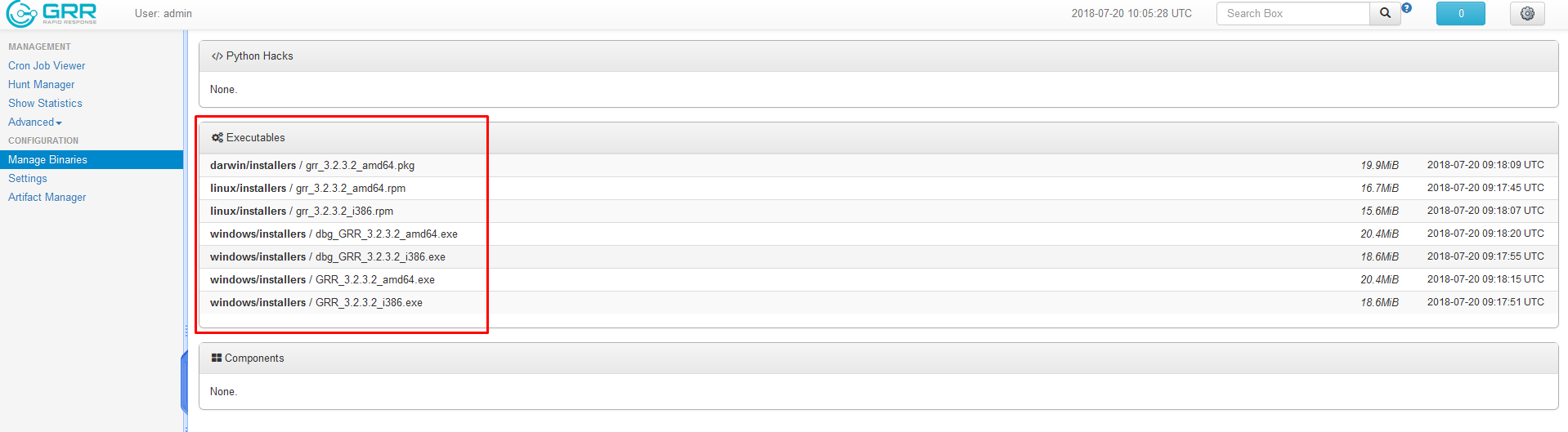
- Select the agent which fits your operating system
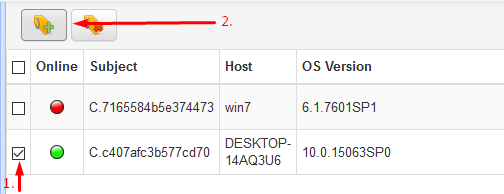
- Create an IP list containing all the hosts you wish to deploy the GRR agent to.
- Using psexec deploy the agents
#psexec @
-u -p -c -f -s - NOTE: For an install without feedback from the agent use the ‘-d’ flag.
- When using psexec, if the executable is not within the Command line environmental path an absolute path or browsing to the containing directory will be required.
- A successful install will return an exit code of 0.
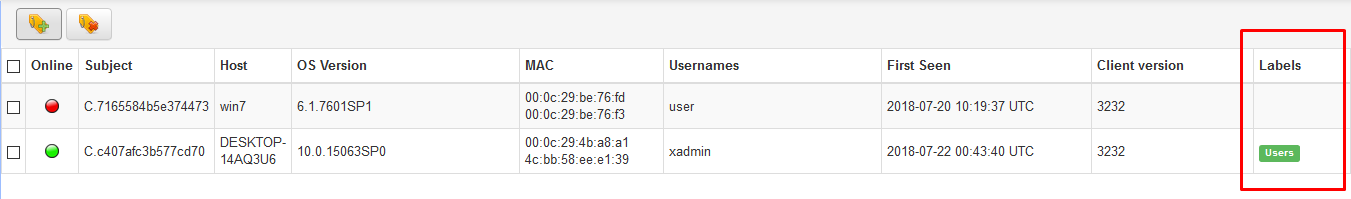
- After successful deployment, be sure to add label to active hosts with a description of what they are.
- Users, Services, SCADA, Etc.
- Users, Services, SCADA, Etc.
For Linux Operating Systems
COMING SOON
Verify Agent communication with Server.
- Using the GRR web ui, use the search bar at the top of the page.
- Leave search bar blank
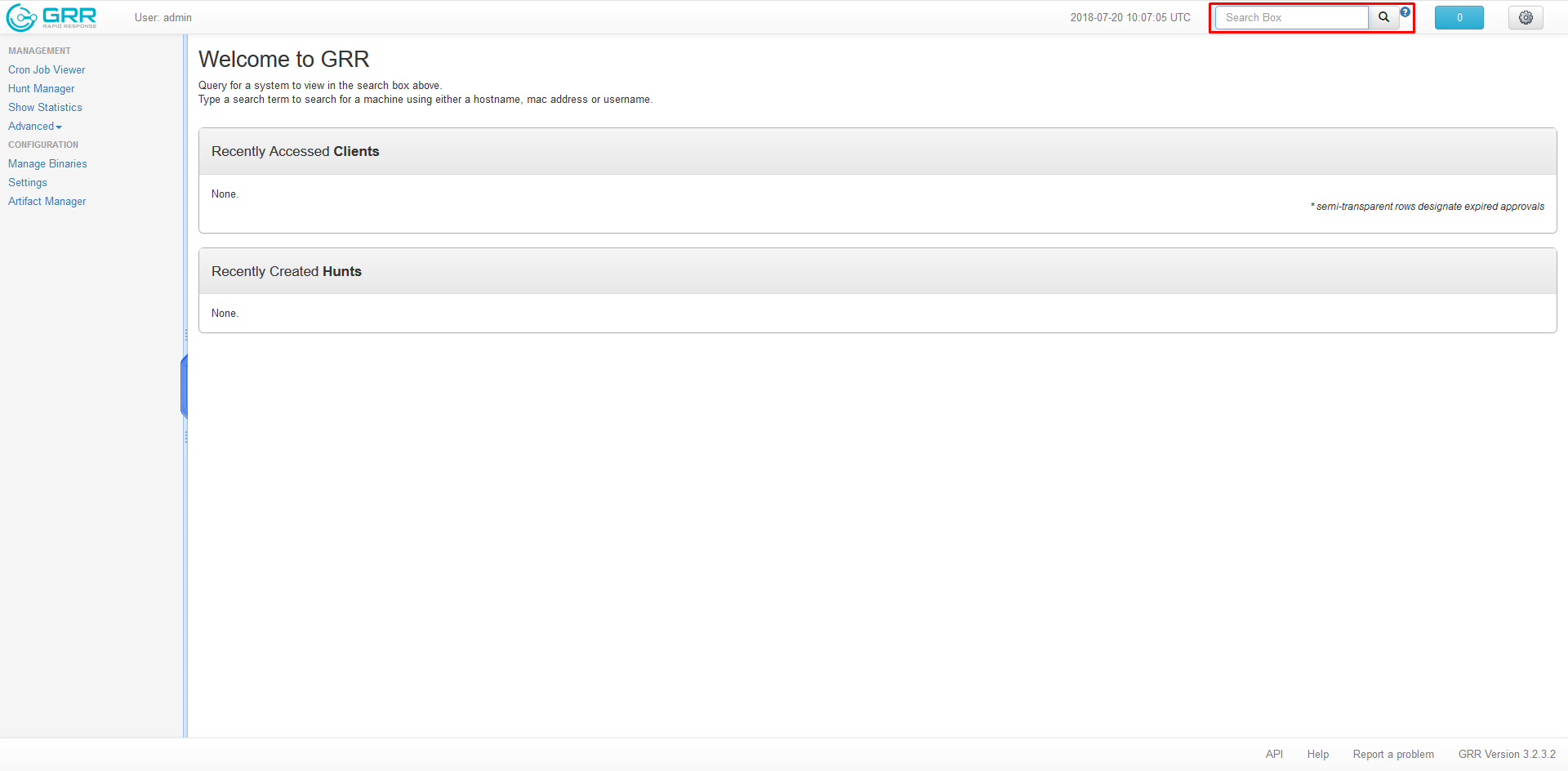
- Press Enter
- The Hosts communicating with the GRR server will be displayed in a list on this page.
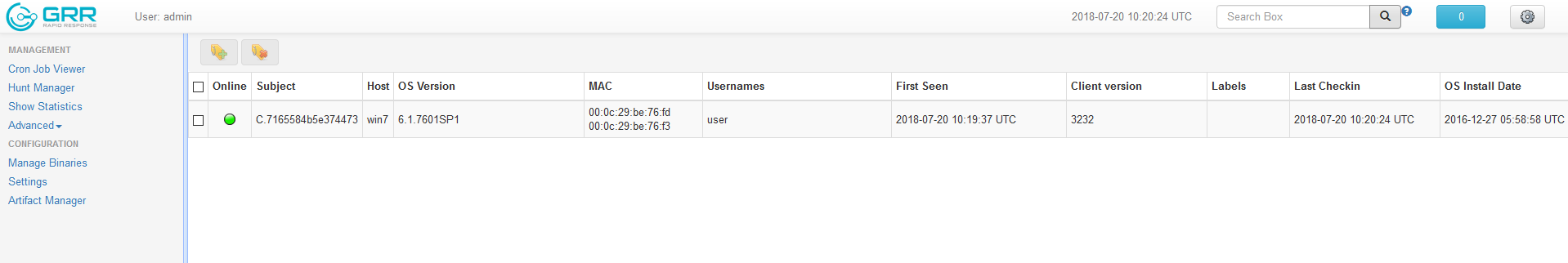
- If a host is not communicating as expected, use ping to determine if the host is active or not.
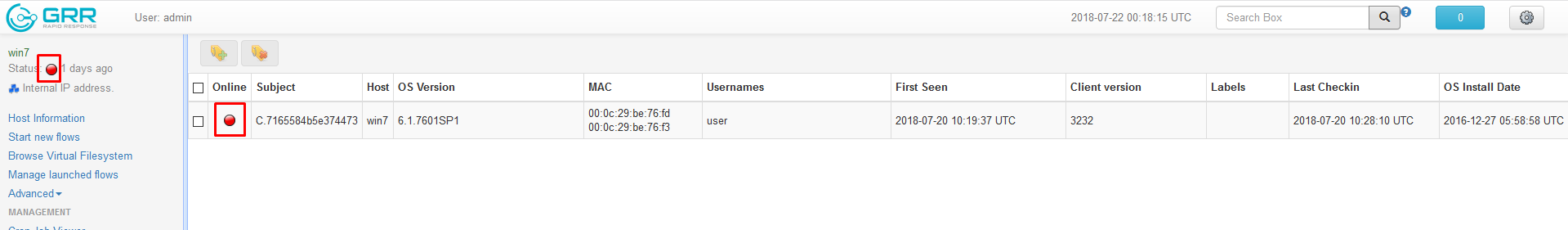
- Determine point of failure if host is active but not calling back to the GRR server.
- verify the GRRservice.exe is running in
tasklistortask manager. * Can the host communicate with the frontend interface of grr usinghttp://x.x.x.x:8080/server.pem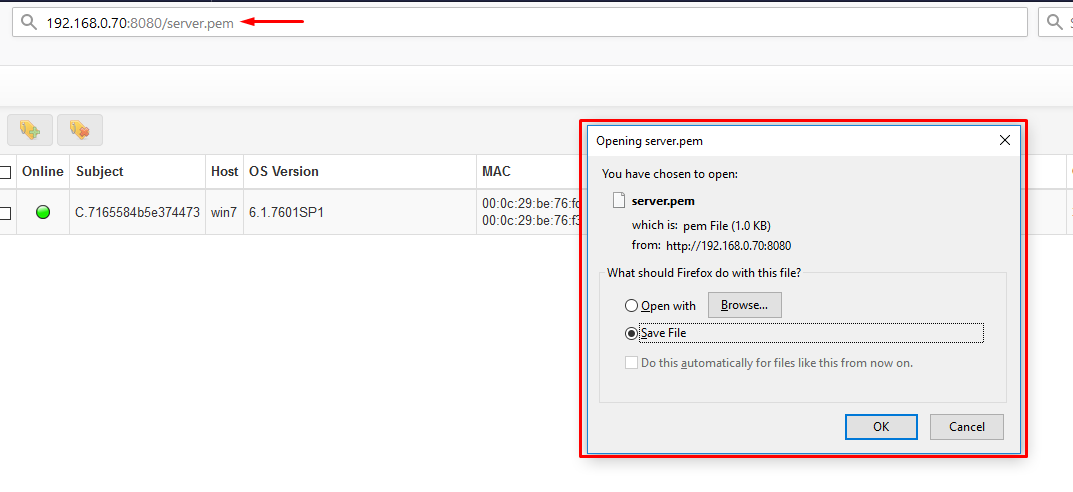
Conducting Analysis Using GRR.
- When starting analysis on one individual host, the analyst should start by interrogating the host for information. This will populate all of the unknown metadata about the host.
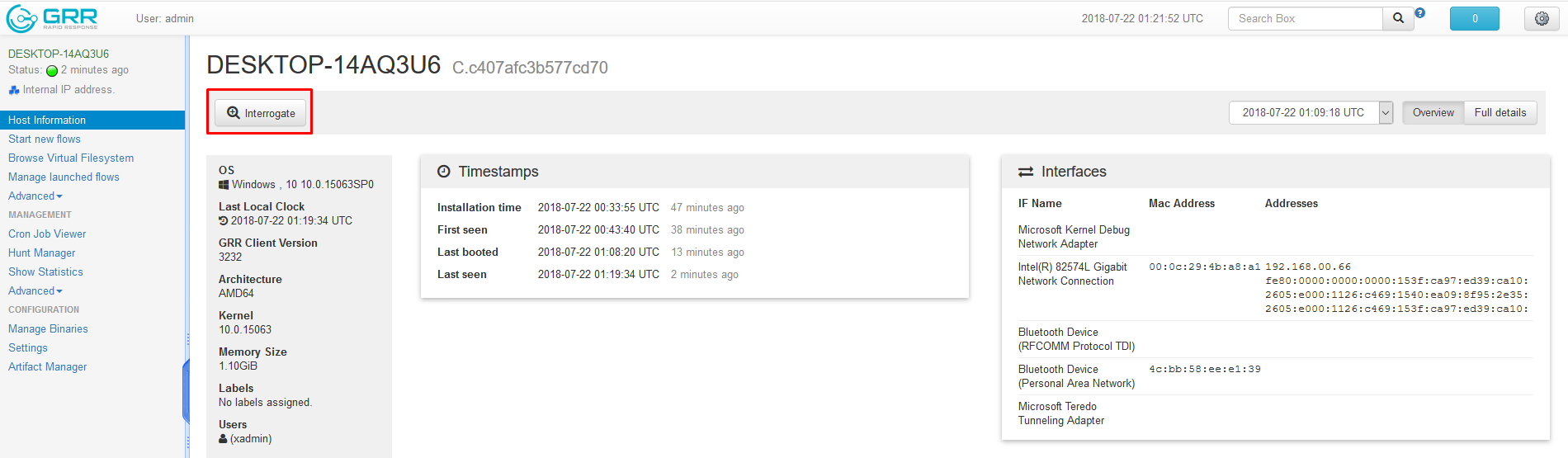
-
Going forward, Hunts can be performed against the hosts. (for example: Task lists and Netstats)
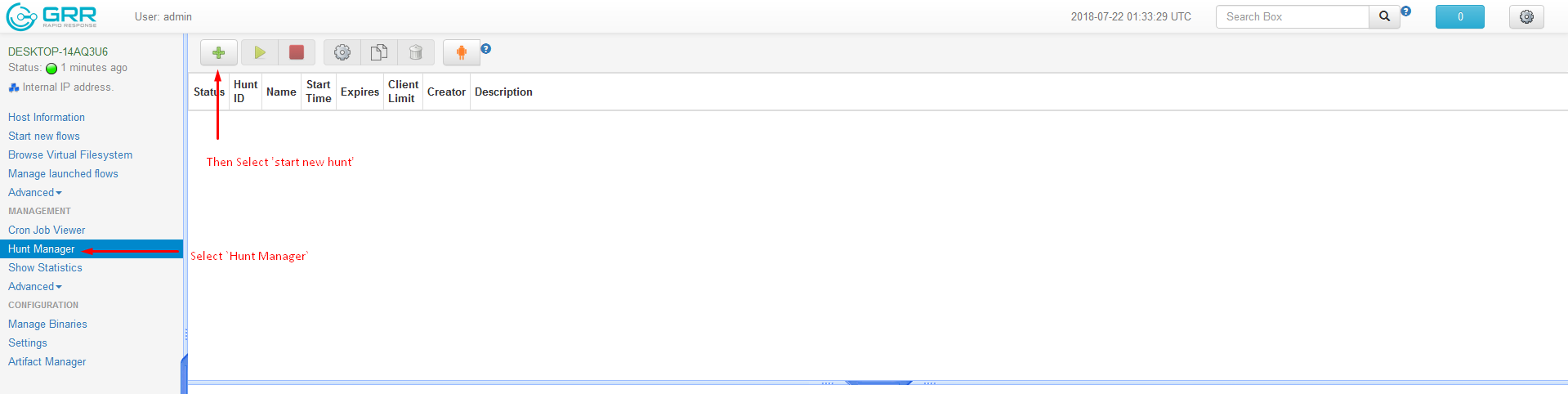
- Running Netstats or Process List against hosts.
- Choose the ‘Hunt Manager’ tab and select the green + or ‘Start new Hunt’
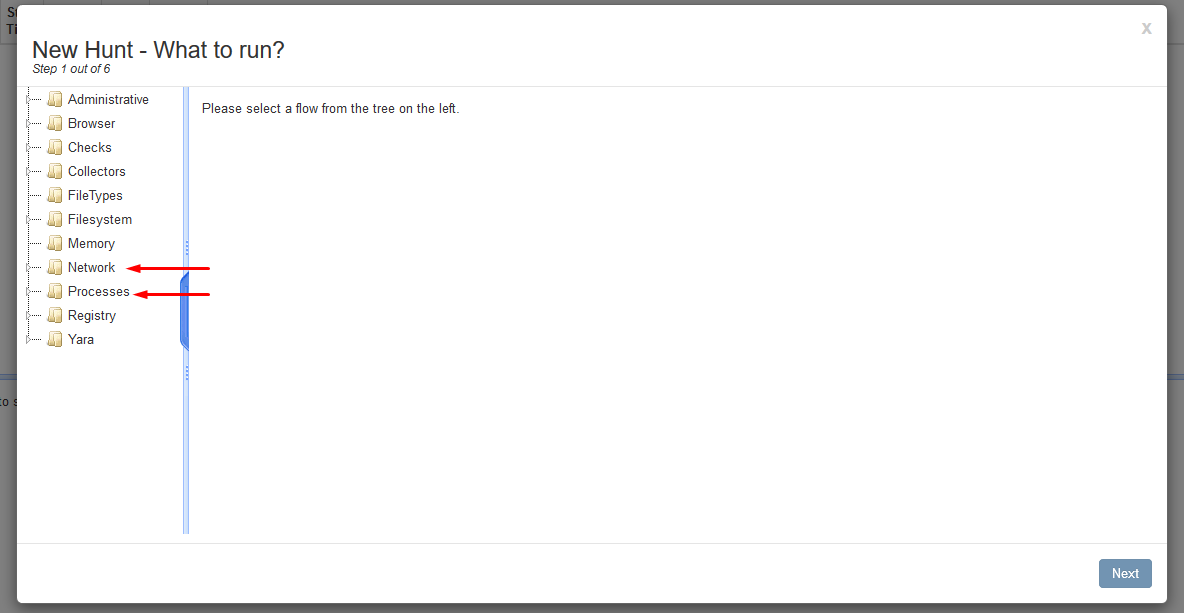
- Select either Network for
netstator Processes fortasklist* For this demonstration we will be running a tasklist but the process is relatively the same for any other hunts. - Select the ListProcesses option then select Next.
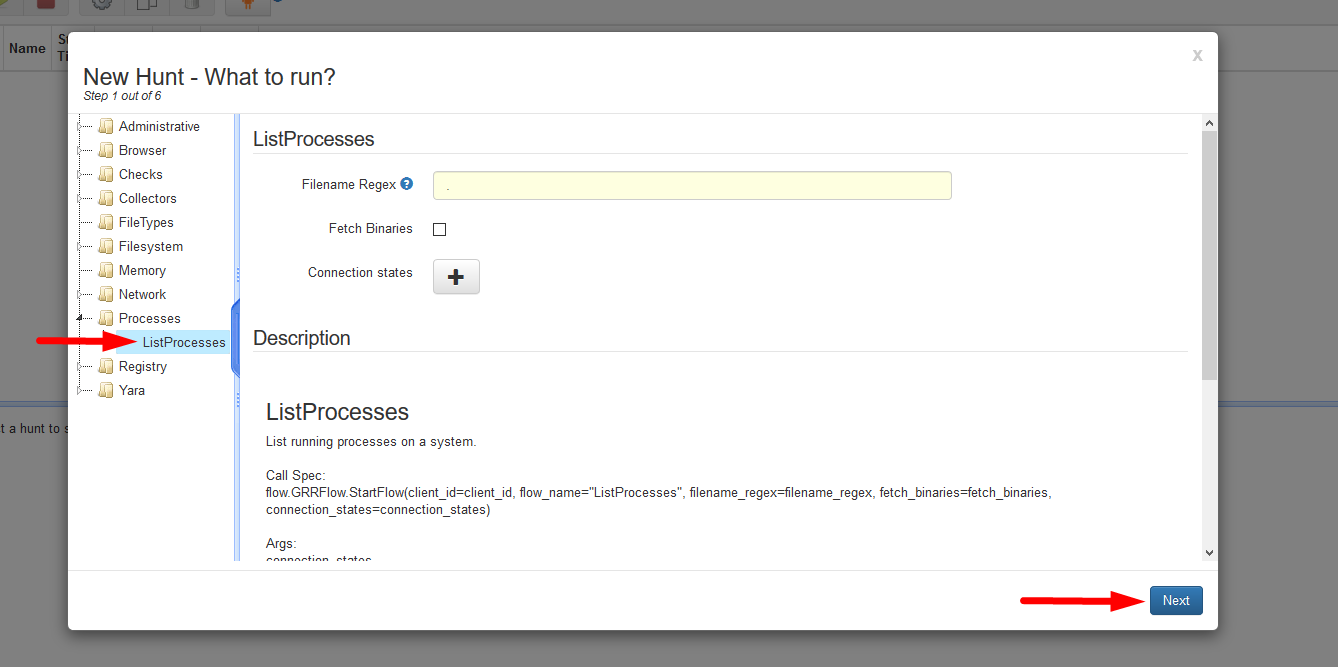
- Enter a description for the Hunt for it to be distinguished in the future then select ‘Next’.
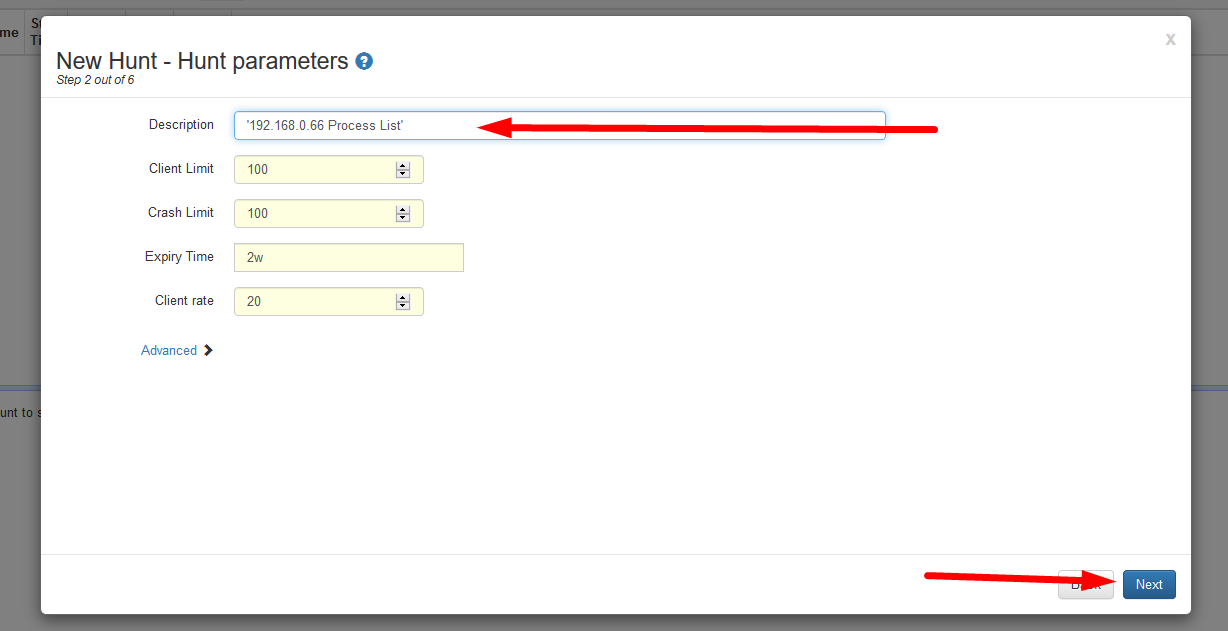
- Unless you have implemented Output plugins, select next.
- This next screen is the ‘Match Mode’ screen this is the where the Grr server will know which hosts you would like to run the hunt against. Select the ‘+’ to add a new match case.
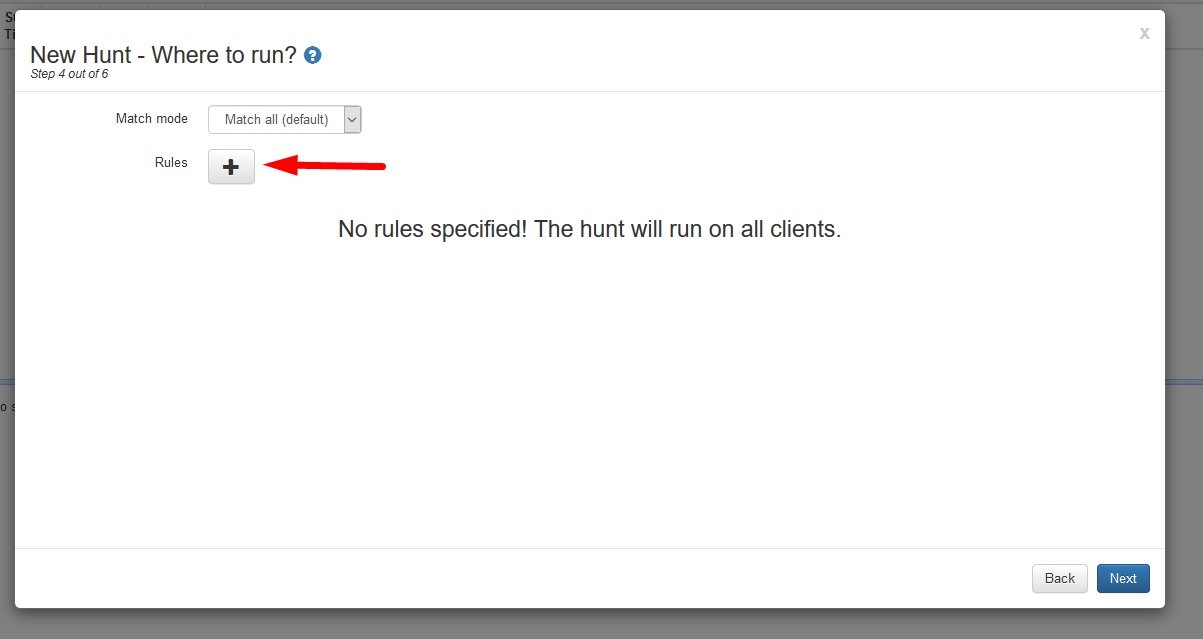 1. There are multiple ways to set up the ‘Match Cases’
1. There are multiple ways to set up the ‘Match Cases’
- By Operating Systems
- By Labels made for the hosts
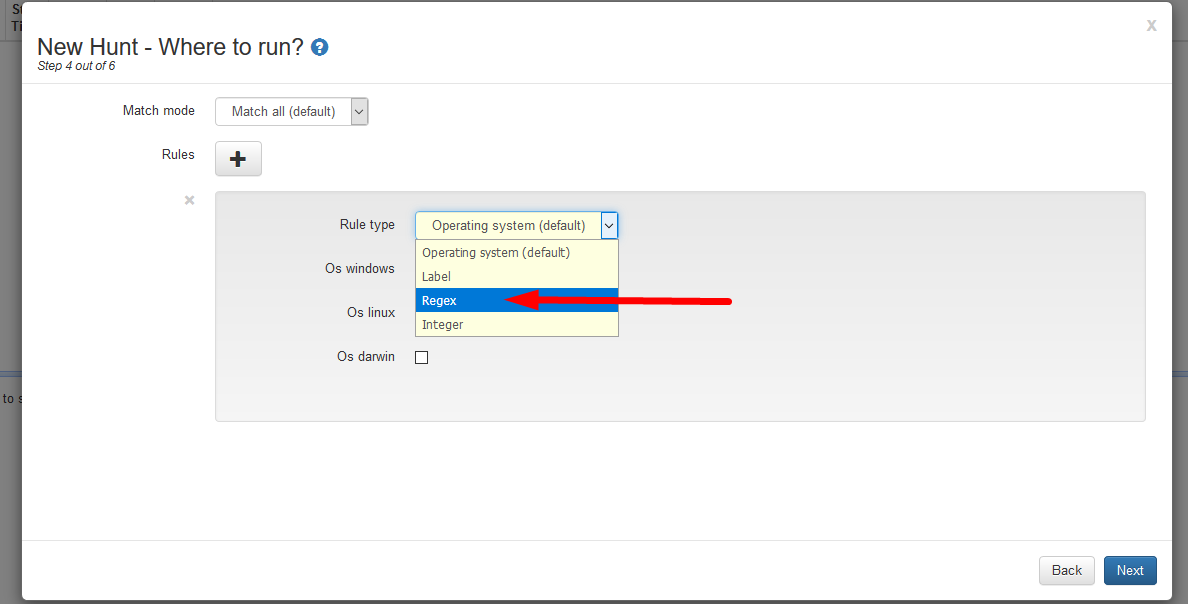
- Or By ‘Regex’ which consists of multiple Cases.
- Choose the Regex option to run against specific IP addresses.
- Under field select
Space seperated list of host IP addresses, and enter the IP address in theAttribute Regexfield then select Next.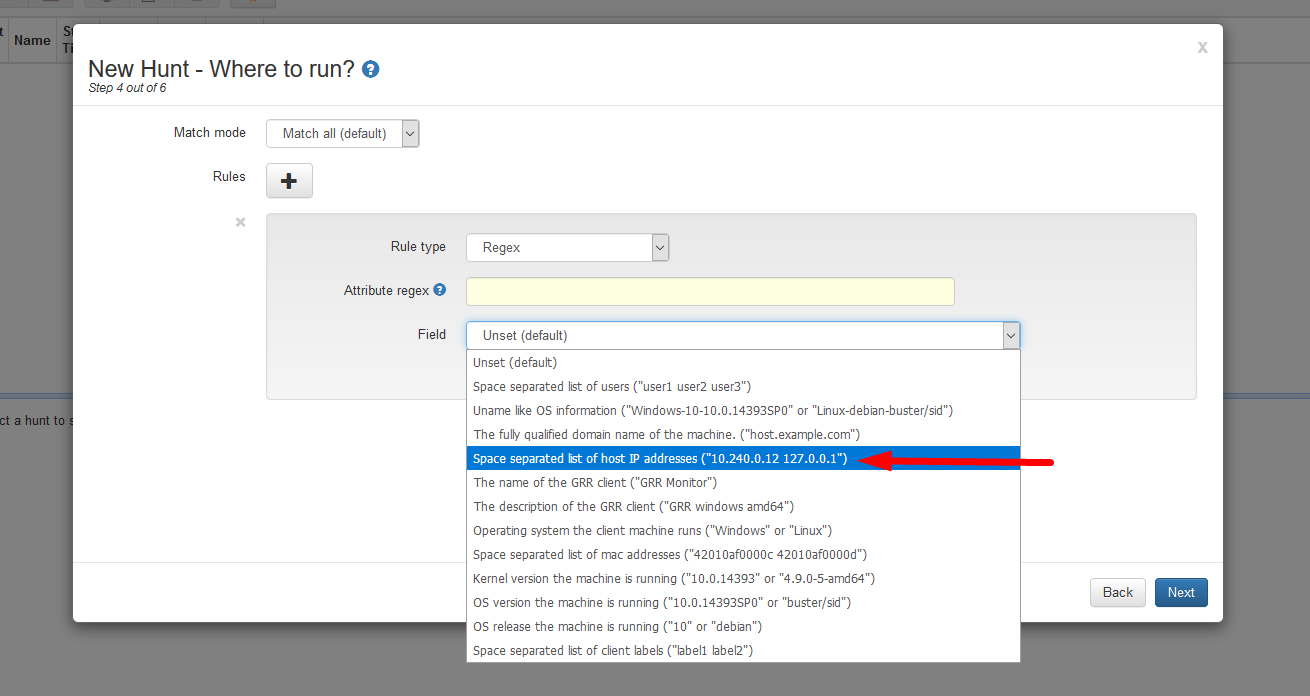
- Choose the Regex option to run against specific IP addresses.
- After selecting ‘Create Hunt’, Select the Hunt and click start.
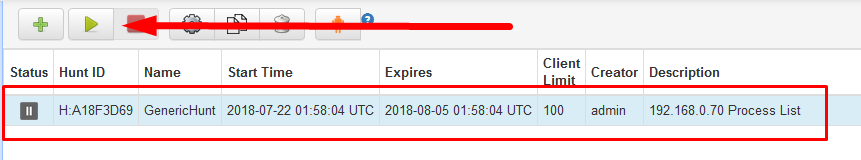
- After the Hunt has completed, Select the hunt again and at the bottom click
Results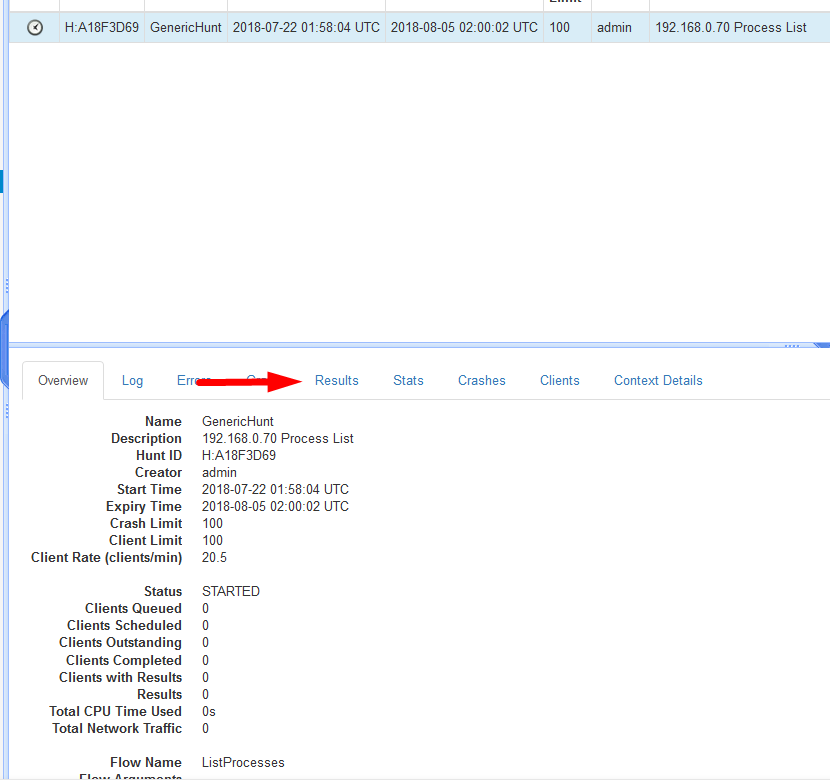
- Choose the ‘Hunt Manager’ tab and select the green + or ‘Start new Hunt’
- Finding a File on a host.
- Choose the ‘Hunt Manager’ tab and select the green + or ‘Start new Hunt’
- Select the
Filesystemoption, thenFile Finder. - Enter the file path, and the action taken against this file then select Next.
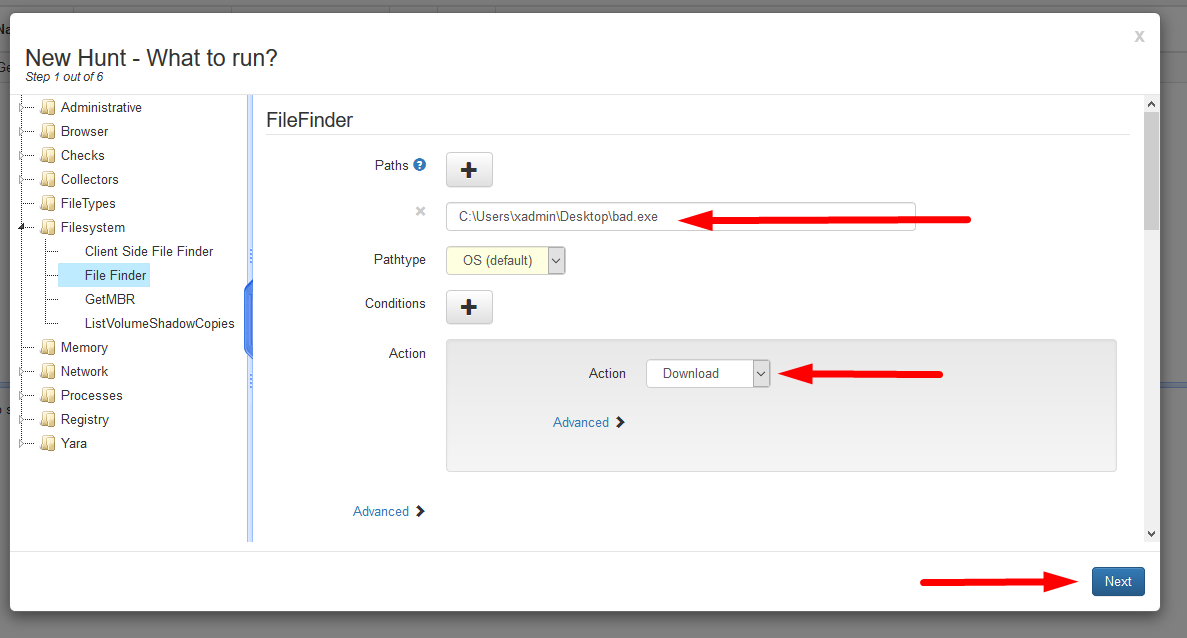
- Enter a description for the Hunt for it to be distinguished in the future then select ‘Next’.
- Unless you have implemented Output plugins, select next.
- This next screen is the ‘Match Mode’ screen this is the where the Grr server will know which hosts you would like to run the hunt against. Select the ‘+’ to add a new match case.
- Choose the Regex option to run against specific IP addresses.
- Under field select
Space seperated list of host IP addresses, and enter the IP address in theAttribute Regexfield then select Next. - After selecting ‘Create Hunt’, Select the Hunt and click start.
- After the Hunt has completed, Select the hunt again and at the bottom click
Results - Browsing the Filesystem of a host.
- After Selecting desired host, Click
Browse Virual Filesystem. Then Select ‘Os’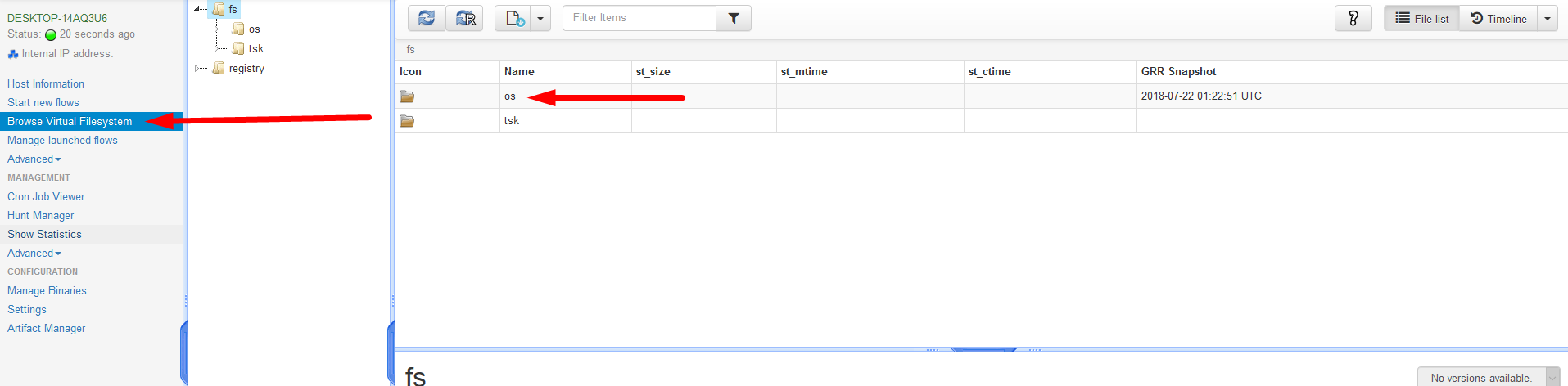
- This will go directly to the main directory where all drives installed on the device will be seen.
* Note the listing will have to be refreshed to populate the folders and files within the drive.
- Running Netstats or Process List against hosts.